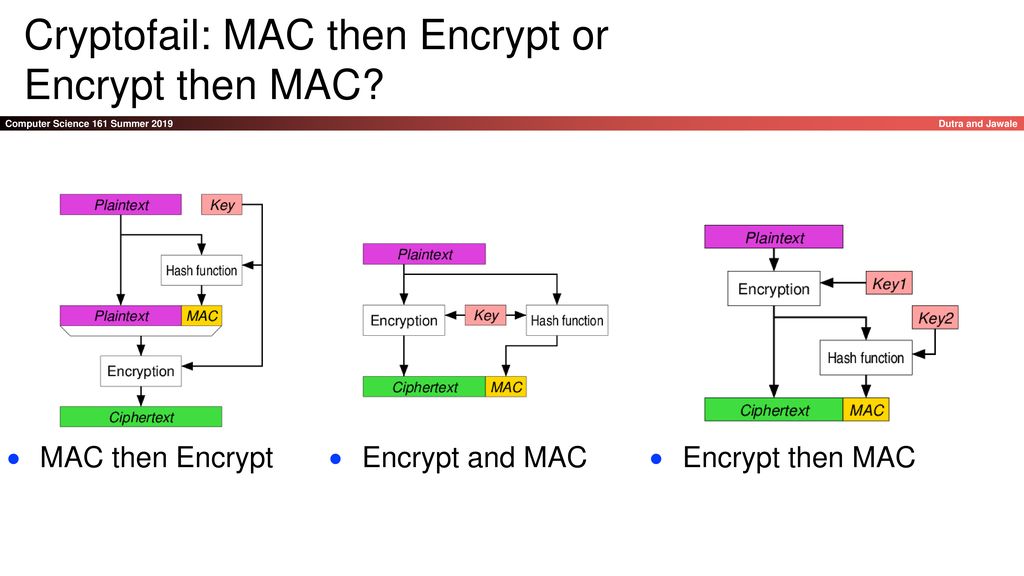
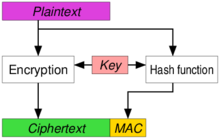
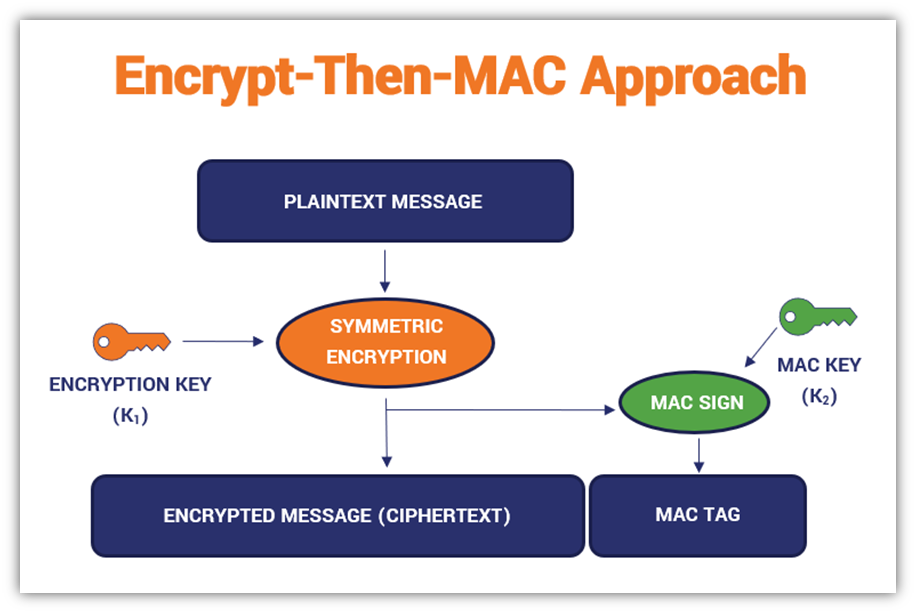
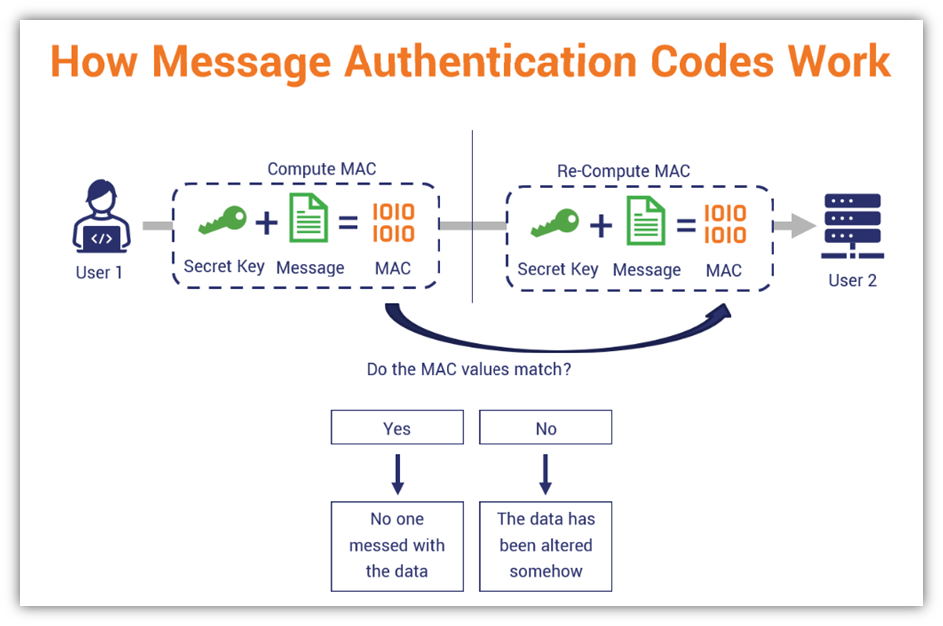
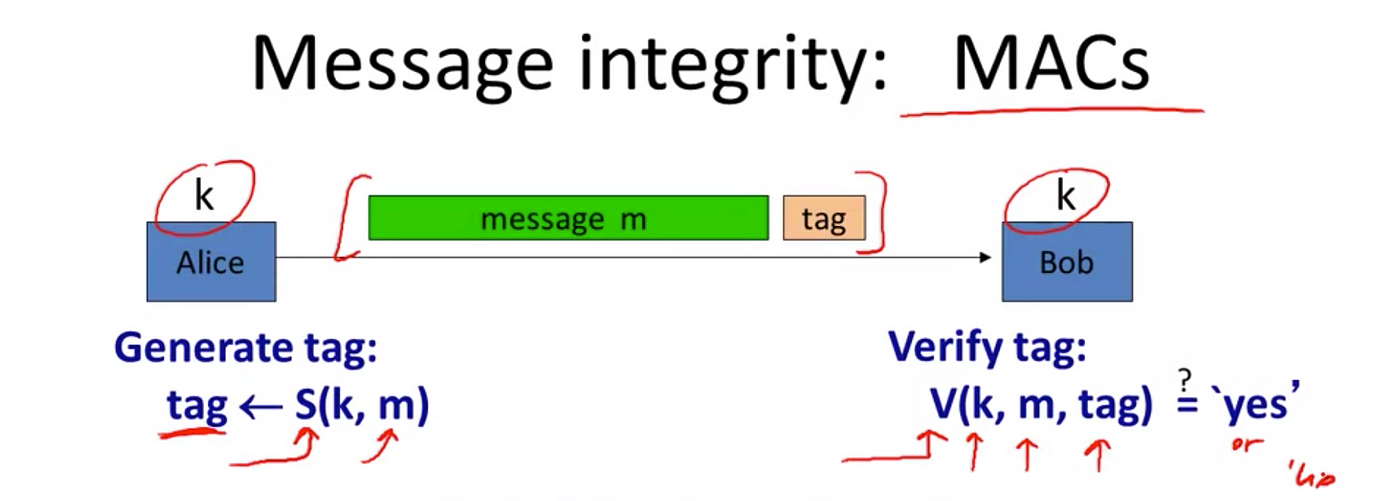
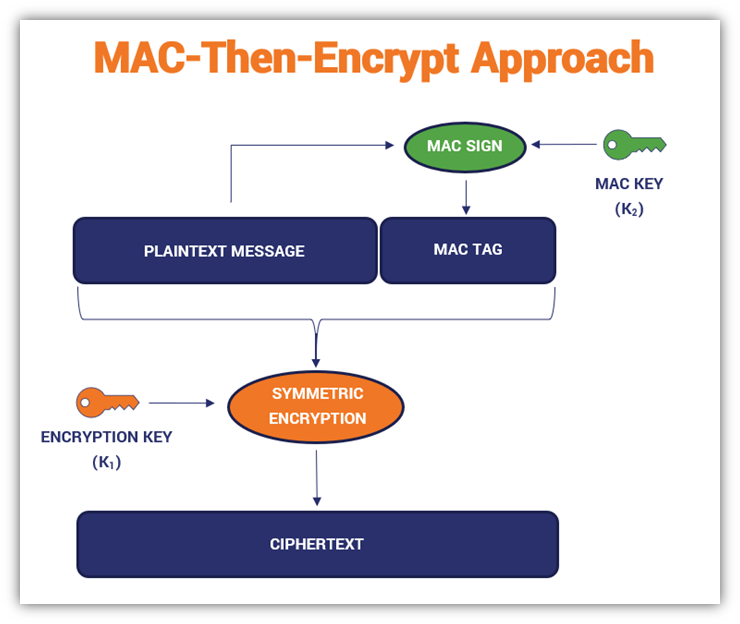
Authenticated Encryption and Cryptographic Network Protocols David Brumley Carnegie Mellon University. - ppt download

Architecture of the security module implementing the Encrypt-then-MAC... | Download Scientific Diagram
GitHub - SoursosK/Encrypt-then-MAC: A demo app applying the Encrypt-then-MAC scheme to a phrase, using AES-CBC 256 and HmacSHA256.

authenticated encryption - Why is a one-time MAC secure for MAC-then-encrypt with randomized-CTR but not randomized-CBC? - Cryptography Stack Exchange
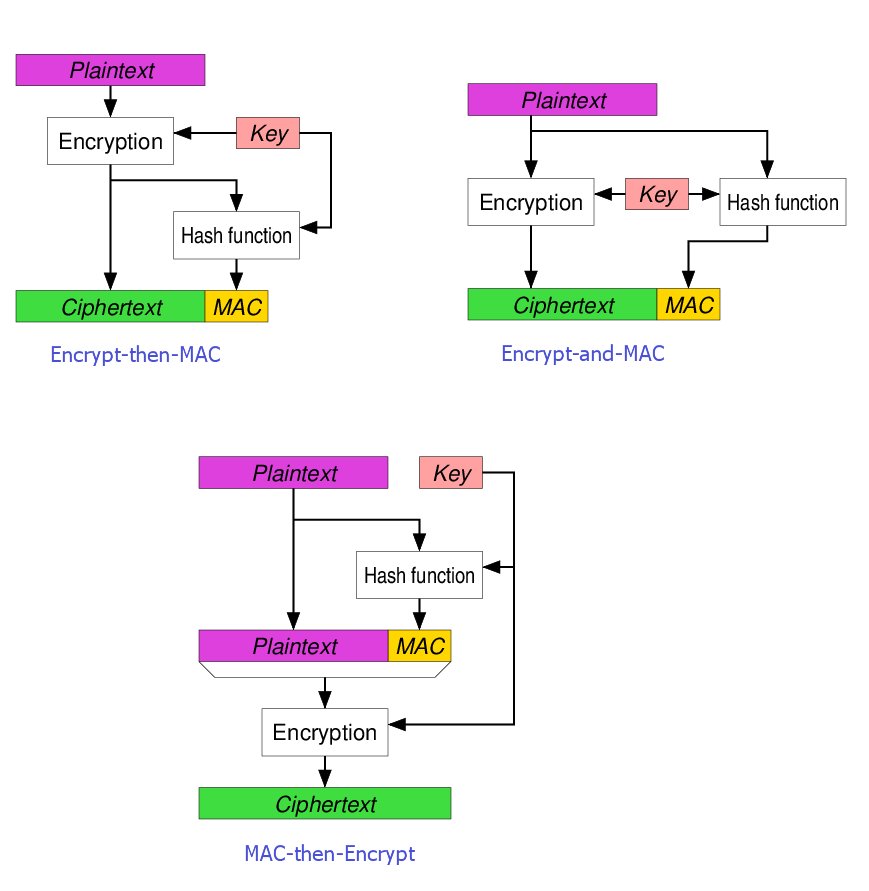
GK Palem on Twitter: "Among the three methods for #Blockchain #Ciphers the Encrypt-Then-MAC has been regarded as the highest definition of security with "strongly unforgeable" MAC, compared with MAC-then-encrypt or Encrypt -and-MAC. Authenticated